A widespread phishing attack hit Gmail users yesterday in a big way. Basically, a bunch of people got emails containing a link to a shared Google Doc. Problem is, if you clicked the link in the email you were actually authorizing hackers to have full access to your Gmail emails and contacts.
Google says they stopped the scheme in about an hour and have completely revoked access to the “Google Docs” app the hackers used to infiltrate accounts. But, if you’re like me, I’d still like to check my account security manually to make sure everything is on the up and up.
Follow KTLA Tech Reporter Rich DeMuro on Facebook or Twitter for cool apps, tech tricks & tips!
Here’s how to do it.
First, go the website https://myaccount.google.com/permissions
Google will likely ask you to re-login to your account for security purposes.
Next, scroll down the list and look for an app called Google Docs. This is confusing since you might use Google Docs for your personal documents. Problem is, Google doesn’t use that naming convention. They use Google Drive, which might also be listed on your account permissions – that one is safe. Something named Google Docs isn’t.
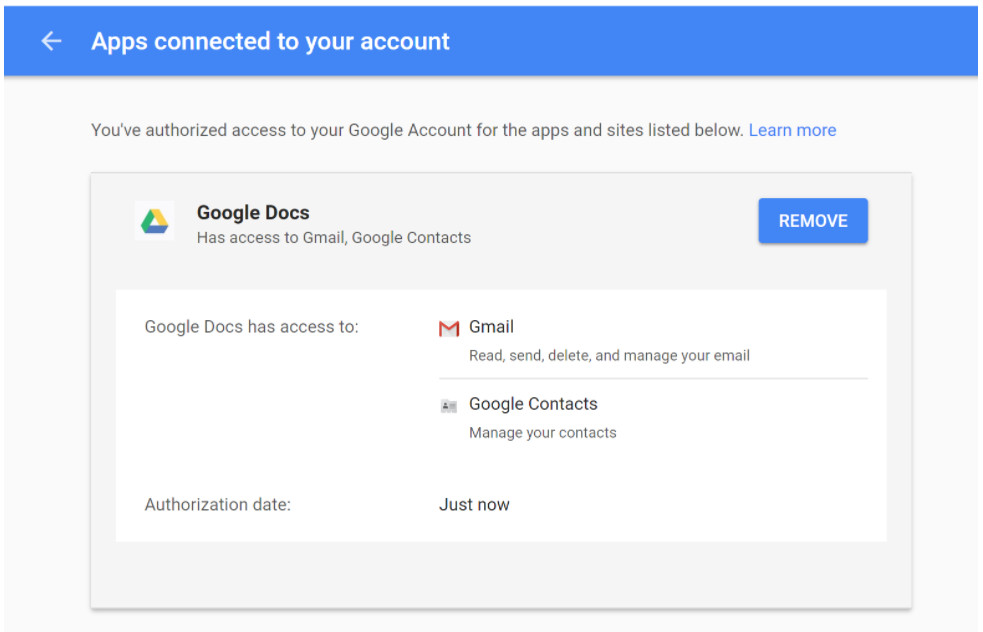
Image courtesy @andrewuf
Since Google deleted access to Google Docs on a global scale, you shouldn’t see it in your list of authorized apps, but in the rare case you do, click it and then click the blue REMOVE button to revoke access.
Since you’re here, it’s also a good idea to remove any apps you don’t recognize or those that no longer need access to your Google account. Take a close look at their permissions – some apps just have access to basic info, which is generally your email address for login purposes, but others have much deeper access. You should be especially interested in any app that has access to “Gmail – Read, send, delete, and manage your email.” If that app is not absolutely necessary to your life, remove it.
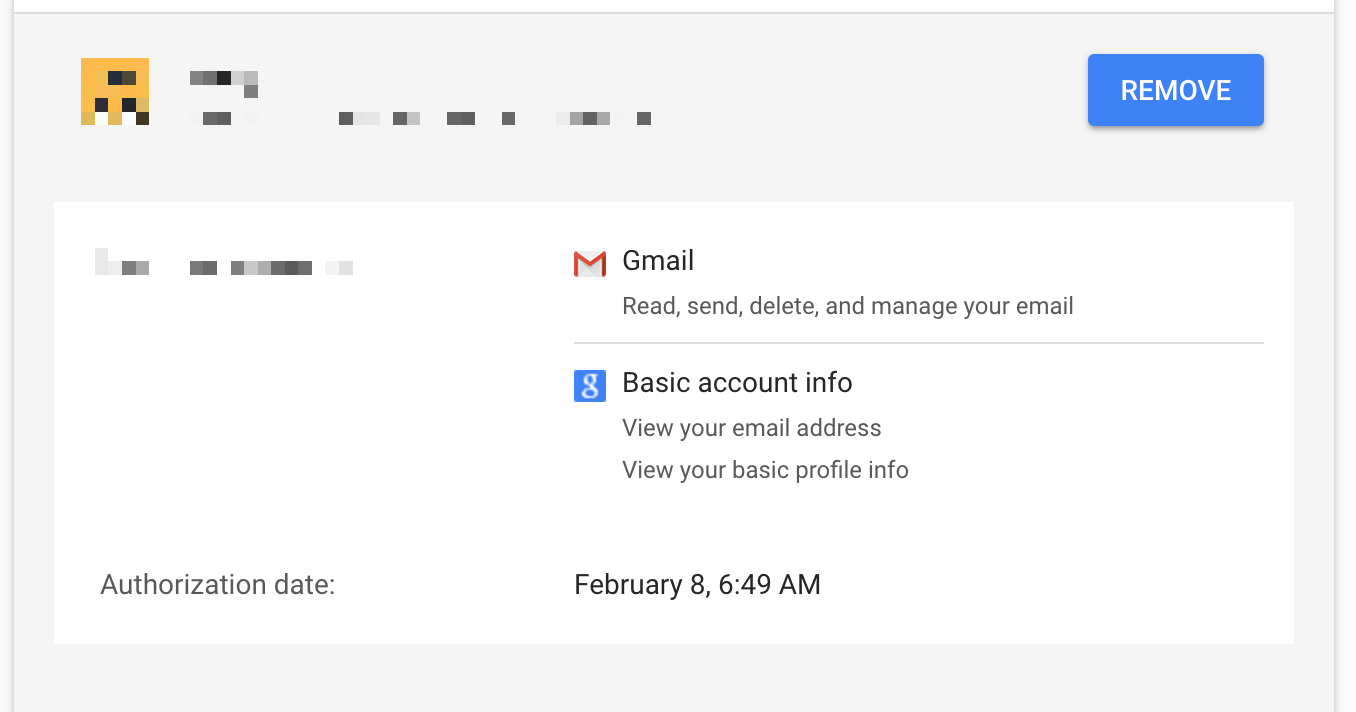
So how did this all happen in the first place? Hackers preyed upon a confusing system. Google, Facebook, Twitter and other major sites allow you to log in to third-party sites in a click so you don’t have to create separate logins. This makes life easier, but you have to be really careful about exactly what you are authorizing. On Facebook, watch for language that says “we can post for on your behalf.” On Google, watch out for anything that requests access beyond basic account info like your email address.
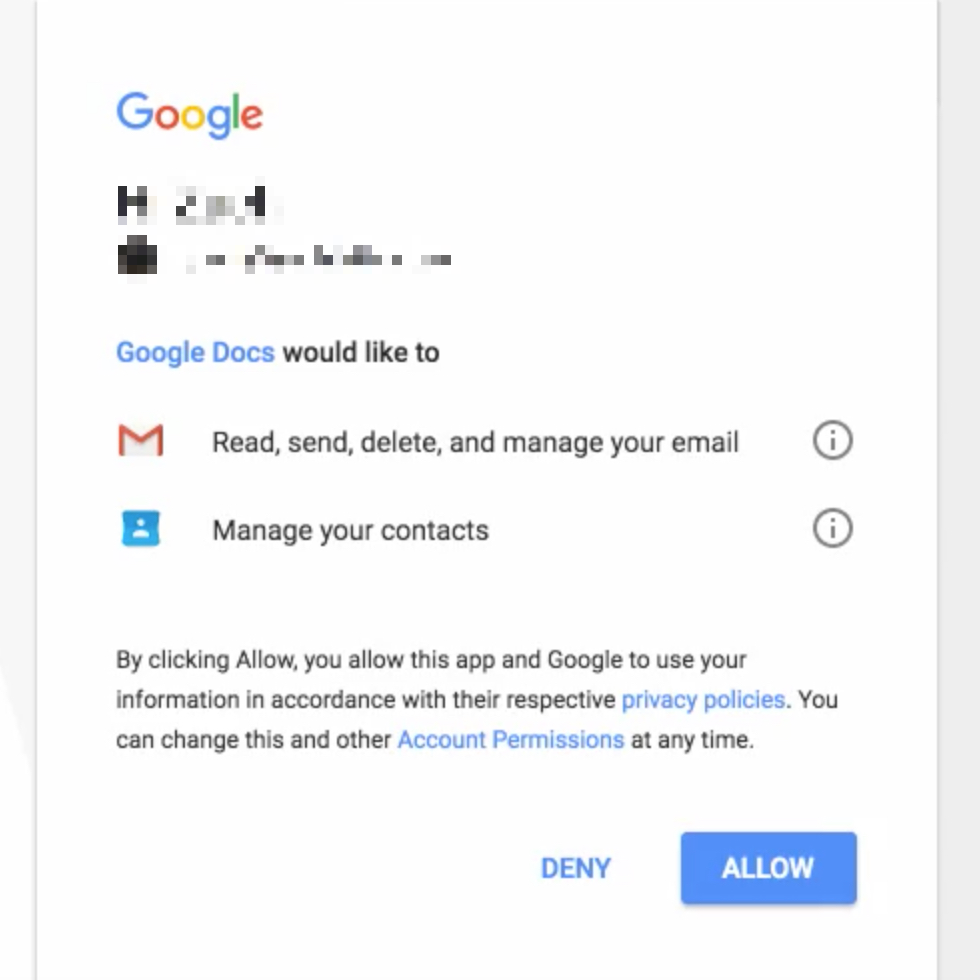
In this case, the authorization screen from hackers requested access to all of Gmail and contacts. Once users said yes, the hacker’s program would automatically grab all of your contacts email addresses and send the phishing email to them. This went on and on and on instantly, so it spread like wildfire.
Bottom line – watch what you click. If you’re not expecting an attachment or shared doc from someone, be weary. Also, be sure to read any screen carefully when you are using one of your major social networks – Google, Twitter, or Facebook – to log into a third-party site.















